Cyber Security Threats: Daily Life as a Developer
When you think of hacking or cyber security threats it probably brings up images of green text dribbling down a screen, or a hooded oddball sat in a dark room typing furiously while code flashes across the monitor.
As Lead Backend developer for Formation Media, I can assure you the reality is far less cinematic and fast-paced. In fact, cyber security is a slow-moving and deliberate process, however, it is also full of wild stories that seem completely divorced from reality.
Security vulnerabilities and cyber security threats
The TSA (Transportation Security Administration) widely known for the long queues they force you into at airports, came under fire earlier this year for a huge vulnerability in one of their vendors that could have been used as a cyber security threat and to gain unlawful access to the cockpits of aircraft.
The root cause of this is 2 systems that the TSA Vendor operates:
- CASS (Cockpit Access Security System) which allows on-duty pilots to travel in the jump seat within the cockpit between airports.
- KCM (Known Crew Member) which is used to identify a person who is permitted to avoid the dreaded security screening.
The Vendor in question is named FlyCASS.com and the vulnerability is one of the simplest attacks within the world of cyber security. The attack is so simple that you could carry out the attack yourself with less than 5 minutes of instruction!
SQL Injection has two parts to understand, first off SQL.
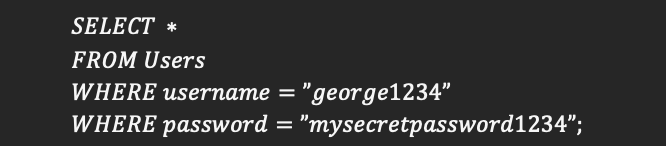
Above is an example of an SQL Query.
- “SELECT *” will retrieve every column of data
- “FROM Users” selects to only look through the Users table
- ‘WHERE username=”george1234”’filters the table to only get rows in which the column for username has a value of “george1234”
- The second “WHERE” filters further to get the row(s) where the password equals my super-secret password that no one will ever guess.
Although the SQL statement above is simplified from what would typically be used in an actual login, it is enough to demonstrate the next section.
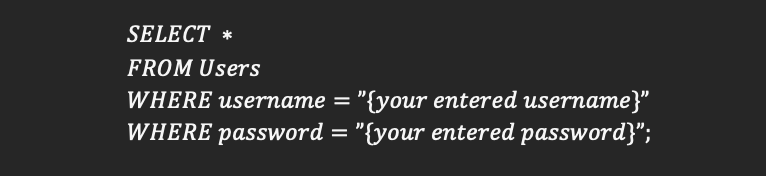
Injection refers here, to the problem. On a login form we would use the data you have entered into the form and replace the values to match for both username and password, but, what if instead of entering a username we entered some SQL code ourselves so we could manipulate what the desired intent is?
We could force the login form to return a user every time without knowing a username and password.
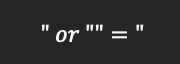
From what we have entered in the image above we can now turn a login SQL query into.
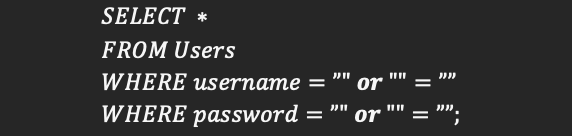
The code will now return all information from every user in the table. If this is tied to some login functionality, we have just logged into the first user in the table.
And for this case we have just gotten past TSA security and into the cockpit of a passenger plane.
You can read more on how to implement an SQL injection attack and more importantly how to prevent it here.
Social engineering attacks
The most common, and unfortunately, hardest type of cyber security threat to stop falls into a category called Social Engineering.
Social Engineering targets the users operating the system rather than the system itself; Phishing emails fall into this category. You have probably been targeted with one of these attacks at some point, hopefully though you saw how illiterate “Microsoft” seemed in the email and ignored it!
A big Social Engineering attack almost happened earlier this year that could have affected a significant amount of the entire internet infrastructure.
The cyber security threat was clever as it targeted a little-known package of code that is part of many Linux operating systems.
The attempted Linux attack
Linux is used on roughly 96% of all servers around the world; connecting to a Linux server requires something called SSH (Secure Shell). This allows you to gain access to the terminal on a Linux machine over the internet, the terminal on Linux is equivalent to your desktop on your home pc.
So, this little package of code was open source and had many contributors, improving and maintaining the package over the years. The guy who owned it originally was getting tired of the responsibility and decided to hand it over to the largest contributor who owned the code repository from then on.
The person he was going to hand it over to turned out to be the attacker! This person implemented many small fixes and pretended to add many more. Once he had control, he added a backdoor that would expose any Linux machine to attack. Luckily a random inquisitive coder found the issue and ensured the matter was dealt with, alerting others so it could be fixed.
Even simpler is an attack that took place during a penetration test in America; the tester called up the helpline and during the process of fixing a fake problem he said something along the lines of “I’m applying for a job near your offices, could you tell me a good place to get lunch?”
He then went to that establishment, where he found a high-level employee eating lunch, cloned his access card with a device no bigger than your wallet and gained unfettered access to the offices!
Ensuring constant vigilance at Formation Media
While working at Formation Media, I have attempted to attack our own systems and the systems we have created for our clients, finding and fixing vulnerabilities before someone who wants to use it for their own personal gain, can.
But we can only make our systems so secure because we know how to be the attacker. We fight a battle every day against cyber security threats, a cat and mouse game of fixes and attacks to ensure our data and our clients data stays away from the Evil Black Hat Hackers out in the world!
If you're concerned about your web security don't hesitate to get in contact with us, and we'll happily discuss the ways to ensure your website remains free from attackers.